OpenStack Neutron/SecurityGroups 学习
- OpenStack 版本: Mitaka
- OpenStack Server OS: CentOS 7
Behavior
入流量 ( ingress ):
- 只有安全组规则匹配的流量会被放行
- 没有安全组规则的时候,所有流量都被丢弃
出流量 ( egress ):
- 只有安全组规则匹配的流量会被放行
- 没有安全组规则的时候,所有流量都被丢弃
- 当安全组被创建时,会有允许所有出流量的规则被创建
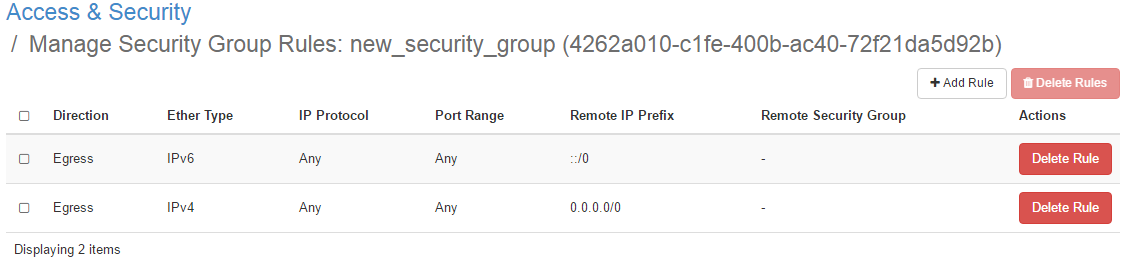
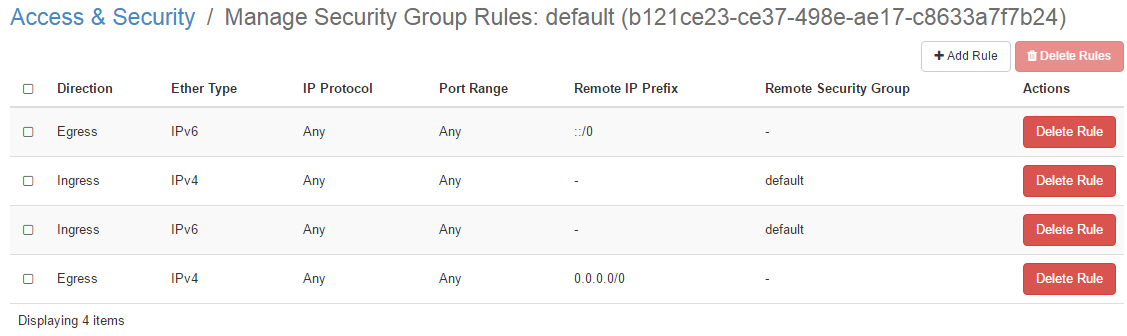
每个租户都会有一个默认安全组 ( default security group ):
- 每个默认安全组都有一条规则用于所有使用了这个默认安全组的 vm 内部通信,即同一个默认安全组的 vm 能互通
- 所有的出流量 ( egress ) 被放行
- 默认安全组以外的入流量 ( ingress ) 被丢弃
Example
-A neutron-openvswi-PREROUTING -m physdev --physdev-in qvbe08f9f5f-e9 -j CT --zone 2
-A neutron-openvswi-PREROUTING -m physdev --physdev-in tape08f9f5f-e9 -j CT --zone 2
:neutron-openvswi-ie08f9f5f-e - [0:0]
:neutron-openvswi-oe08f9f5f-e - [0:0]
:neutron-openvswi-se08f9f5f-e - [0:0]
-A neutron-openvswi-FORWARD -m physdev --physdev-out tape08f9f5f-e9 --physdev-is-bridged -m comment --comment "Direct traffic from the VM interface to the security group chain." -j neutron-openvswi-sg-chain
-A neutron-openvswi-FORWARD -m physdev --physdev-in tape08f9f5f-e9 --physdev-is-bridged -m comment --comment "Direct traffic from the VM interface to the security group chain." -j neutron-openvswi-sg-chain
-A neutron-openvswi-INPUT -m physdev --physdev-in tape08f9f5f-e9 --physdev-is-bridged -m comment --comment "Direct incoming traffic from VM to the security group chain." -j neutron-openvswi-oe08f9f5f-e
-A neutron-openvswi-ie08f9f5f-e -m state --state RELATED,ESTABLISHED -m comment --comment "Direct packets associated with a known session to the RETURN chain." -j RETURN
-A neutron-openvswi-ie08f9f5f-e -s 172.21.1.132/32 -p udp -m udp --sport 67 -m udp --dport 68 -j RETURN
-A neutron-openvswi-ie08f9f5f-e -s 172.21.1.124/32 -p udp -m udp --sport 67 -m udp --dport 68 -j RETURN
-A neutron-openvswi-ie08f9f5f-e -s 172.21.1.127/32 -p udp -m udp --sport 67 -m udp --dport 68 -j RETURN
-A neutron-openvswi-ie08f9f5f-e -s 172.21.1.125/32 -p udp -m udp --sport 67 -m udp --dport 68 -j RETURN
-A neutron-openvswi-ie08f9f5f-e -m set --match-set NIPv463aa6169-0b6b-4c8e-afde- src -j RETURN
-A neutron-openvswi-ie08f9f5f-e -p tcp -m tcp --dport 3389 -j RETURN
-A neutron-openvswi-ie08f9f5f-e -p tcp -m tcp --dport 22 -j RETURN
-A neutron-openvswi-ie08f9f5f-e -m state --state INVALID -m comment --comment "Drop packets that appear related to an existing connection (e.g. TCP ACK/FIN) but do not have an entry in conntrack." -j DROP
-A neutron-openvswi-ie08f9f5f-e -m comment --comment "Send unmatched traffic to the fallback chain." -j neutron-openvswi-sg-fallback
-A neutron-openvswi-oe08f9f5f-e -s 0.0.0.0/32 -d 255.255.255.255/32 -p udp -m udp --sport 68 --dport 67 -m comment --comment "Allow DHCP client traffic." -j RETURN
-A neutron-openvswi-oe08f9f5f-e -j neutron-openvswi-se08f9f5f-e
-A neutron-openvswi-oe08f9f5f-e -p udp -m udp --sport 68 --dport 67 -m comment --comment "Allow DHCP client traffic." -j RETURN
-A neutron-openvswi-oe08f9f5f-e -p udp -m udp --sport 67 -m udp --dport 68 -m comment --comment "Prevent DHCP Spoofing by VM." -j DROP
-A neutron-openvswi-oe08f9f5f-e -m state --state RELATED,ESTABLISHED -m comment --comment "Direct packets associated with a known session to the RETURN chain." -j RETURN
-A neutron-openvswi-oe08f9f5f-e -j RETURN
-A neutron-openvswi-oe08f9f5f-e -m state --state INVALID -m comment --comment "Drop packets that appear related to an existing connection (e.g. TCP ACK/FIN) but do not have an entry in conntrack." -j DROP
-A neutron-openvswi-oe08f9f5f-e -m comment --comment "Send unmatched traffic to the fallback chain." -j neutron-openvswi-sg-fallback
-A neutron-openvswi-se08f9f5f-e -s 172.21.1.134/32 -m mac --mac-source FA:16:3E:59:58:1D -m comment --comment "Allow traffic from defined IP/MAC pairs." -j RETURN
-A neutron-openvswi-se08f9f5f-e -m comment --comment "Drop traffic without an IP/MAC allow rule." -j DROP
-A neutron-openvswi-sg-chain -m physdev --physdev-out tape08f9f5f-e9 --physdev-is-bridged -m comment --comment "Jump to the VM specific chain." -j neutron-openvswi-ie08f9f5f-e
-A neutron-openvswi-sg-chain -m physdev --physdev-in tape08f9f5f-e9 --physdev-is-bridged -m comment --comment "Jump to the VM specific chain." -j neutron-openvswi-oe08f9f5f-e
-A neutron-openvswi-sg-fallback -m comment --comment "Default drop rule for unmatched traffic." -j DROP表 neutron-openvswi-ie08f9f5f-e 用于过滤进入 vm 的流量。
表 neutron-openvswi-oe08f9f5f-e 用于过滤从 vm 出的流量。
其中 neutron-openvswi-o 和 neutron-openvswi-i 的 i 和 o 表示进和出,e08f9f5f-e 为 port_id 的前几位。
-A neutron-openvswi-ie08f9f5f-e -s 172.21.1.132/32 -p udp -m udp --sport 67 -m udp --dport 68 -j RETURN
-A neutron-openvswi-ie08f9f5f-e -s 172.21.1.124/32 -p udp -m udp --sport 67 -m udp --dport 68 -j RETURN
-A neutron-openvswi-ie08f9f5f-e -s 172.21.1.127/32 -p udp -m udp --sport 67 -m udp --dport 68 -j RETURN
-A neutron-openvswi-ie08f9f5f-e -s 172.21.1.125/32 -p udp -m udp --sport 67 -m udp --dport 68 -j RETURN
-A neutron-openvswi-oe08f9f5f-e -s 0.0.0.0/32 -d 255.255.255.255/32 -p udp -m udp --sport 68 --dport 67 -m comment --comment "Allow DHCP client traffic." -j RETURN
-A neutron-openvswi-oe08f9f5f-e -p udp -m udp --sport 68 --dport 67 -m comment --comment "Allow DHCP client traffic." -j RETURNDHCP 流量放行,DHCP Server 端口 UDP / 67, DHCP Client 端口 UDP / 68.
-A neutron-openvswi-oe08f9f5f-e -p udp -m udp --sport 67 -m udp --dport 68 -m comment --comment "Prevent DHCP Spoofing by VM." -j DROP防止 vm DHCP 欺骗攻击。
-A neutron-openvswi-ie08f9f5f-e -m set --match-set NIPv463aa6169-0b6b-4c8e-afde- src -j RETURN# ipset list
Name: NIPv463aa6169-0b6b-4c8e-afde-
Type: hash:net
Revision: 3
Header: family inet hashsize 1024 maxelem 65536
Size in memory: 16848
References: 2
Members:
172.21.1.134
172.21.1.135remote-group ( 远端安全组 ) 的 vm 流量放行。
-A neutron-openvswi-oe08f9f5f-e -j neutron-openvswi-se08f9f5f-e
-A neutron-openvswi-se08f9f5f-e -s 172.21.1.134/32 -m mac --mac-source FA:16:3E:59:58:1D -m comment --comment "Allow traffic from defined IP/MAC pairs." -j RETURN出 vm 的流量只有源 ip 和 mac 与 vm 的 ip 和 mac 匹配才放行。
-A neutron-openvswi-ie08f9f5f-e -m state --state INVALID -m comment --comment "Drop packets that appear related to an existing connection (e.g. TCP ACK/FIN) but do not have an entry in conntrack." -j DROP
-A neutron-openvswi-sg-fallback -m comment --comment "Default drop rule for unmatched traffic." -j DROP没有匹配的流量被丢弃。
Port allowed-address-pairs
由于 Neutron 只允许 mac_address 和 ip_address 匹配的流量通过。例如 VRRP 协议的 vip 无法直接作用在 vm 里,需要配置 allowed-address-pairs 来允许指定 mac_address/ip_address(CIDR)对,使它们可以在不考虑子网的情况下通过一个端口。
创建一个带有 allowed-address-pairs 的端口:
neutron port-create net-id --allowed-address-pairs type=dict list=true ip_address=<ip_cidr>[,mac_address=<mac_address>]给已创建的端口添加 allowed-address-pairs:
neutron port-update port-uuid --allowed-address-pairs type=dict list=true ip_address=<ip_cidr>,[mac_address=<mac_address>]Security Group custom ICMP
在调用 API 或者命令行创建 security group rules 时,参数 port-range-min 为 ICMP type, 参数 port-range-max 为 ICMP code.
全部为空为 ALL ICMP.
Type 和 Code 的配置可见下表:
| Type | Code | Status | Description |
|---|---|---|---|
| 0 – Echo Reply | 0 | Echo reply (used to ping) | |
| 1 and 2 | unassigned | Reserved | |
| 3 – Destination Unreachable | 0 | Destination network unreachable | |
| 1 | Destination host unreachable | ||
| 2 | Destination protocol unreachable | ||
| 3 | Destination port unreachable | ||
| 4 | Fragmentation required, and DF flag set | ||
| 5 | Source route failed | ||
| 6 | Destination network unknown | ||
| 7 | Destination host unknown | ||
| 8 | Source host isolated | ||
| 9 | Network administratively prohibited | ||
| 10 | Host administratively prohibited | ||
| 11 | Network unreachable for ToS | ||
| 12 | Host unreachable for ToS | ||
| 13 | Communication administratively prohibited | ||
| 14 | Host Precedence Violation | ||
| 15 | Precedence cutoff in effect | ||
| 4 – Source Quench | 0 | deprecated | Source quench (congestion control) |
| 5 – Redirect Message | 0 | Redirect Datagram for the Network | |
| 1 | Redirect Datagram for the Host | ||
| 2 | Redirect Datagram for the ToS & network | ||
| 3 | Redirect Datagram for the ToS & host | ||
| 6 | deprecated | Alternate Host Address | |
| 7 | unassigned | Reserved | |
| 8 – Echo Request | 0 | Echo request (used to ping) | |
| 9 – Router Advertisement | 0 | Router Advertisement | |
| 10 – Router Solicitation | 0 | Router discovery/selection/solicitation | |
| 11 – Time Exceeded | 0 | TTL expired in transit | |
| 1 | Fragment reassembly time exceeded | ||
| 12 – Parameter Problem: Bad IP header | 0 | Pointer indicates the error | |
| 1 | Missing a required option | ||
| 2 | Bad length | ||
| 13 – Timestamp | 0 | Timestamp | |
| 14 – Timestamp Reply | 0 | Timestamp reply | |
| 15 – Information Request | 0 | deprecated | Information Request |
| 16 – Information Reply | 0 | deprecated | Information Reply |
| 17 – Address Mask Request | 0 | deprecated | Address Mask Request |
| 18 – Address Mask Reply | 0 | deprecated | Address Mask Reply |
| 19 | reserved | Reserved for security | |
| 20 through 29 | reserved | Reserved for robustness experiment | |
| 30 – Traceroute | 0 | deprecated | Information Request |
| 31 | deprecated | Datagram Conversion Error | |
| 32 | deprecated | Mobile Host Redirect | |
| 33 | deprecated | Where-Are-You (originally meant for IPv6) | |
| 34 | deprecated | Here-I-Am (originally meant for IPv6) | |
| 35 | deprecated | Mobile Registration Request | |
| 36 | deprecated | Mobile Registration Reply | |
| 37 | deprecated | Domain Name Request | |
| 38 | deprecated | Domain Name Reply | |
| 39 | deprecated | SKIP Algorithm Discovery Protocol, Simple Key-Management for Internet Protocol | |
| 40 | Photuris, Security failures | ||
| 41 | experimental | ICMP for experimental mobility protocols such as Seamoby [RFC4065] | |
| 42 through 252 | unassigned | Reserved | |
| 253 | experimental | RFC3692-style Experiment 1 (RFC 4727) | |
| 254 | experimental | RFC3692-style Experiment 2 (RFC 4727) | |
| 255 | reserved | Reserved |